Most VPN advice online is misleading; and believing it can leave you less secure than you think.
After years of testing VPNs and helping clients improve their privacy, I’ve seen how some providers use flashy marketing to oversell benefits and hide important limitations.
The truth? Some VPN companies promise “complete anonymity” or “military-grade security” but bury the fine print that reveals speed drops, weaker protections, and gaps that hackers, advertisers, or even governments can exploit.
Key Takeaways
- Why “complete anonymity” claims are impossible and dangerous to believe
- How free VPN services actually make money from your private data
- The tracking methods that work even when your IP address is hidden
- Why every VPN connection slows down your internet
- How law enforcement can still identify VPN users when they need to
- The critical security differences between consumer and business VPNs
- Red flags that reveal when your VPN is actually compromising your privacy

How VPNs Actually Work
Before we dive into the myths, let’s establish what VPNs actually do versus what marketing departments claim they do.
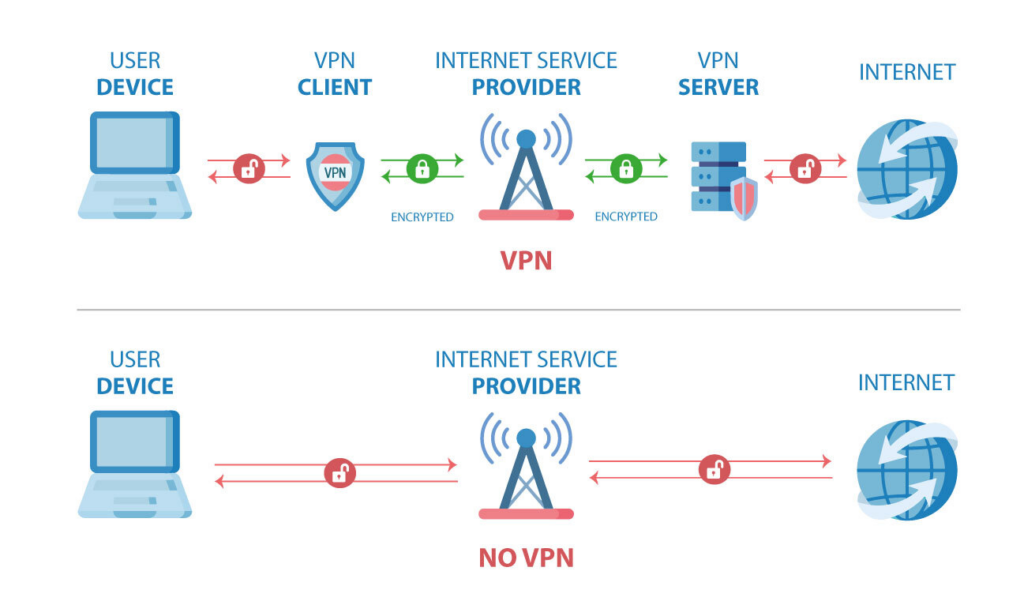
A Virtual Private Network creates an encrypted tunnel between your device and a remote server. Think of it like mailing a letter in a locked box instead of a transparent envelope.
Without a VPN: Your device connects directly to websites, and your internet provider can see every site you visit, when you visit it, and how long you stay.
With a VPN: Your device sends encrypted data to the VPN server first, then the server forwards your requests to websites. Your internet provider only sees encrypted traffic going to one server.
This basic function provides real privacy benefits, but it also creates new vulnerabilities and dependencies that most people never consider.
What are DNS Leaks?
The DNS Leak Problem Everyone Ignores…
Here’s a vulnerability that affects millions of VPN users without them knowing it.
Before your device can connect to any website, it needs to translate the domain name (like “google.com”) into an IP address that computers understand. This translation happens through Domain Name System (DNS) requests.
The problem? Many devices send these DNS requests directly to your internet provider’s servers, completely bypassing your VPN tunnel.
What this means: Even with your VPN running, your internet provider can still see every website you’re trying to visit through these leaked DNS requests.
Test it yourself: Visit dnsleaktest.com while connected to your VPN. If you see your internet provider’s name or your real location in the results, your DNS requests are leaking.
Quality services like NordVPN include automatic DNS leak protection, but cheaper providers often skip this feature or neglect it entirely.
Myth #1: “VPNs Make Me Completely Anonymous Online”
The marketing claim: VPN advertisements frequently promise “complete anonymity,” “invisible browsing,” and “untraceable internet activity.”
Why this is dangerous: You’re not anonymous; you’ve just transferred your trust from your internet provider to your VPN company.
When you connect to a VPN, your provider gains access to the same information your internet provider used to see:
- Your real IP address and physical location
- Exact timestamps of when you connect and disconnect
- Every website you visit and how long you spend there
- Your total bandwidth usage and traffic patterns
- Payment information that directly links to your identity
The best VPN companies implement strict no-logs policies and undergo independent security audits. But they still have the technical capability to monitor everything you do online.
The bottom line: VPNs provide privacy by hiding your activity from internet providers and local network administrators. They don’t provide anonymity.
Myth #2: “Free VPNs Are Fine for Basic Privacy Protection”
The appeal: Why pay for privacy when you can get it free?
The reality: Free VPN services need revenue to operate, and since users don’t pay directly, they monetize your data in ways that completely defeat the purpose of using a VPN.
Here’s how free VPNs actually make money:
- Selling browsing data: Many free services log your internet activity and sell detailed browsing profiles to advertising networks
- Injecting advertisements: Some free VPNs modify web pages to insert additional ads, earning commission on clicks
- Malware distribution: The most aggressive free services bundle malware or adware with their applications
- Bandwidth theft: Some providers use your device as an exit node for other users’ traffic
Security researchers have documented free VPN services owned by data analytics companies that sell user browsing patterns within hours of collection.
The irony: Free VPNs often expose you to more privacy violations than using no VPN at all.
Myth #3: “My VPN Stops All Online Tracking”
The assumption: Since VPNs hide IP addresses, websites can’t track users anymore.
What actually happens: Modern web tracking uses dozens of identification methods that work perfectly fine regardless of your IP address.
Websites can still track you through:
- Browser fingerprinting: Your screen resolution, installed fonts, browser version, plugins, and system settings create a unique signature that’s often more reliable than IP addresses
- Persistent cookies and local storage: Data files that survive browser sessions and identify returning users
- Account logins: Signing into Gmail, Facebook, Amazon, or any other service immediately identifies you regardless of your IP address
- Cross-site tracking scripts: Social media widgets and embedded content that follow you across different websites
In practical terms, I can visit 20 different websites using VPN connections from various countries, and tracking services will still identify me as the same user on most sites using fingerprinting techniques.
Key takeaway: VPNs block IP-based tracking but can’t prevent the more sophisticated methods that most websites actually use.
Myth #4: “Premium VPNs Don’t Slow Down Your Internet”
The marketing promise: “Lightning-fast speeds” and “no performance impact” appear in almost every VPN advertisement.
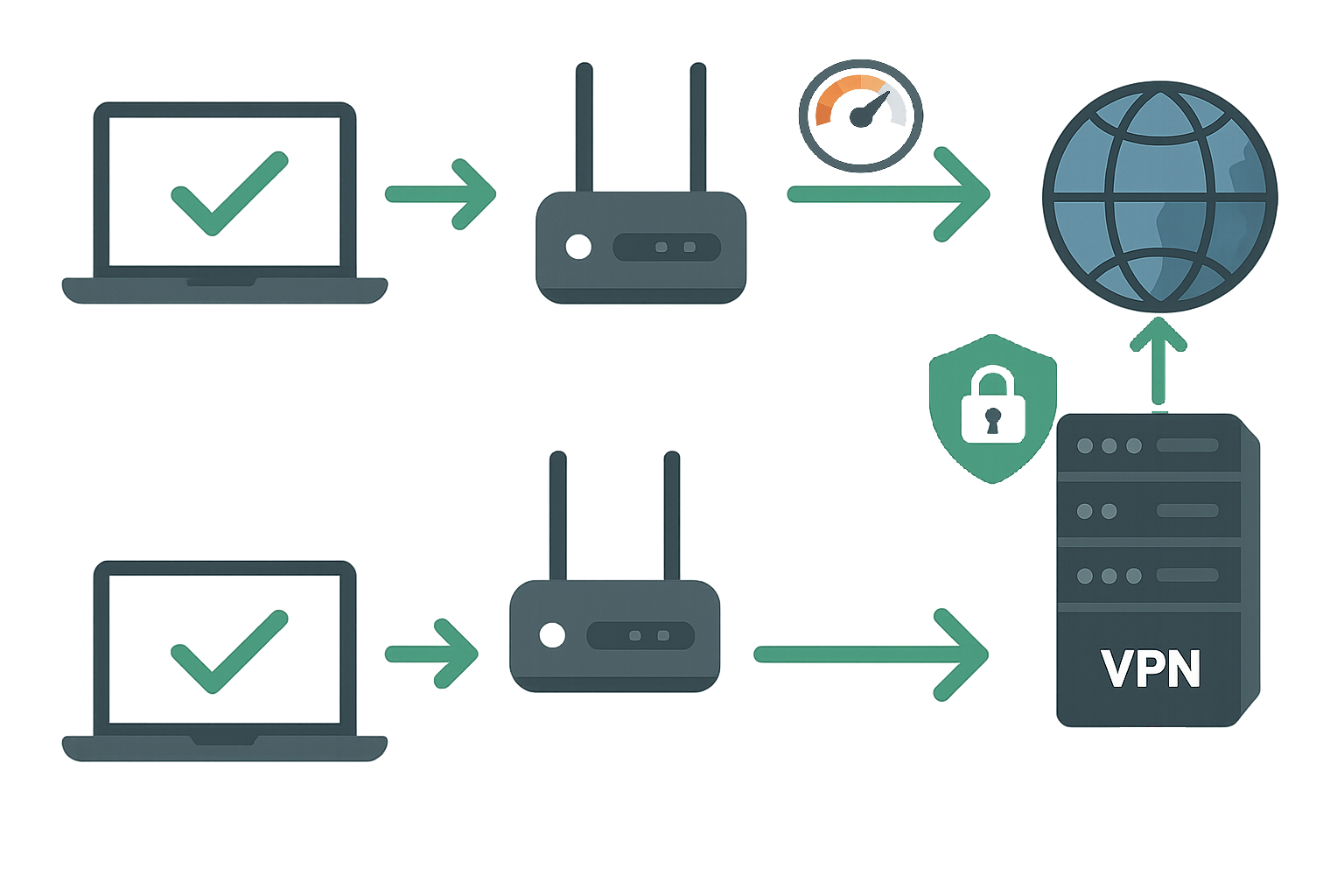
The physics reality: Every VPN connection inherently reduces internet speed due to encryption overhead and increased routing distance.
Without VPN: Your Device → Internet Provider → Website
With VPN: Your Device → Internet Provider → VPN Server → Website
According to recent testing by Wirecutter (The New York Times), speed reduction varies significantly between VPN providers, with NordVPN achieving the best scores in their comprehensive testing:
- NordVPN (top performer): Only 7% latency increase, 12% download reduction, 4% upload reduction
- Other premium services: 23-42% latency increase, 13-26% download reduction
- Budget providers: 50-67% latency increase, 16-40% download reduction
- Lowest-tier services: Up to 486% latency increase with similar download impacts
These results demonstrate why choosing a quality VPN provider makes a significant difference in maintaining usable internet speeds while protecting your privacy.
Speed reduction happens because of:
- Encryption processing: Your device needs CPU power to encrypt and decrypt data packets
- Geographic distance: Physical distance between you and the VPN server location
- Server capacity: How many users are sharing the same server resources
- Protocol overhead: Extra data required for secure tunneling
Quality providers minimize speed loss through optimized networks and efficient protocols, but some reduction is inevitable. Anyone claiming otherwise is lying.
Myth #5: “All VPN Security Is Basically the Same”
The confusion: VPN marketing emphasizes similar features like “military-grade encryption” across different providers.
The truth: VPN security implementation varies dramatically between providers, with major differences in encryption quality, logging policies, and additional protections.
| Security Feature | Premium Providers | Budget Services | Free VPNs |
|---|---|---|---|
| Encryption Standard | AES-256 with perfect forward secrecy | AES-256 (basic implementation) | Often weaker or outdated |
| Kill Switch | Application and system-level protection | Basic disconnect feature | Usually absent |
| DNS Protection | Built-in leak prevention + custom DNS | Basic leak prevention | Frequently leaks DNS requests |
| Logging Policy | Independently audited no-logs | Varies widely | Extensive logging common |
| Server Infrastructure | Owned servers or vetted providers | Mixed third-party servers | Overcrowded shared servers |
The most important differentiators include third-party security audits, open-source implementations, legal jurisdiction, and warrant canary policies that alert users to government requests.
Business consideration: If you’re protecting company data, consumer VPNs often lack the centralized management and compliance features required for business environments.
Myth #6: “VPNs Make Me Untraceable to Law Enforcement”
The media narrative: High-profile cases where VPNs appear to provide complete protection from government surveillance.
The operational reality: Government agencies have multiple methods for identifying VPN users when they have legal authority and sufficient resources.
Law enforcement can identify VPN users through:
- VPN provider cooperation: Court orders can compel providers to start logging specific users or provide real-time monitoring
- Payment trail analysis: Credit card transactions, PayPal accounts, and banking records directly link VPN subscriptions to real identities
- Traffic correlation analysis: Monitoring data patterns and timing relationships between VPN entry and exit points
- Device fingerprinting: Hardware and software characteristics that remain consistent across VPN connections
- Endpoint surveillance: Monitoring the destination servers or websites being accessed
VPN providers in Five Eyes countries (US, UK, Canada, Australia, New Zealand) operate under intelligence sharing agreements and potential government pressure.
Bottom line: VPNs protect against routine surveillance and mass data collection but don’t guarantee immunity from targeted law enforcement investigations.
Myth #7: “Consumer VPNs Work Fine for Business Use”
The small business assumption: If a VPN provides privacy for personal use, it should work fine for business operations.
The compliance reality: Business and personal VPN requirements differ significantly in security standards, administrative controls, and regulatory compliance.
Critical business requirements that consumer VPNs typically don’t provide:
- Centralized user management: IT administrators need to create accounts, manage permissions, and revoke access for multiple employees
- Compliance documentation: Industries like healthcare and finance require VPNs that meet specific regulatory standards (HIPAA, SOX, PCI-DSS)
- Activity logging for security: Businesses often need detailed connection logs for security auditing and incident response
- Dedicated infrastructure: Business plans include dedicated servers and guaranteed bandwidth allocations
- Integration capabilities: Business VPNs need to work with existing firewalls, security tools, and network infrastructure
The fundamental difference: Consumer VPNs prioritize individual privacy and ease of use. Business VPNs prioritize organizational security and administrative control.
Small businesses handling sensitive client data should evaluate business-grade solutions rather than assuming consumer VPN services provide adequate organizational security.
What Actually Makes a VPN Trustworthy
After years of evaluating VPN services for both personal and client use, these features separate trustworthy providers from marketing-heavy services:
- Independently audited no-logs policy: Third-party verification by reputable security firms, not just marketing claims
- Kill switch functionality: Automatic internet disconnection if the VPN connection fails
- Strong encryption standards: AES-256 encryption with secure key exchange protocols
- DNS leak protection: Built-in prevention of DNS requests bypassing the VPN tunnel
- Jurisdiction considerations: Provider location outside aggressive surveillance jurisdictions
- Transparent security practices: Regular security audits, bug bounty programs, and open-source implementations
VPN Recommendations Based on Testing
After extensive evaluation across multiple use cases and threat models:
For Personal Privacy: NordVPN consistently demonstrates reliable performance, verified security practices, and comprehensive privacy protection. Their independently audited no-logs policy and strong encryption implementation provide trustworthy privacy protection for personal use.
For Budget-Conscious Users: IPVanish VPN offers competitive performance with current promotions that include additional security features like free eSIM services for mobile users.
For Business Applications: Organizations requiring integrated security solutions should consider enterprise platforms that combine VPN functionality with business password management and administrative controls.
Pricing strategy: Annual subscription plans from established providers offer significantly better value than monthly billing while maintaining security standards. Avoid free services that compromise privacy for cost savings.

Building a Complete Privacy Strategy
VPNs provide valuable privacy protection by encrypting internet connections and hiding IP addresses from websites and local network surveillance.
However, they represent one component of comprehensive privacy protection, not a complete solution for online security.
Effective privacy requires combining VPNs with additional practices:
- Browser privacy settings and ad blockers to prevent tracking scripts
- Secure messaging applications for private communications
- Careful social media management and privacy controls
- Regular security audits of online accounts and passwords
- Understanding the privacy policies of services you actually use
Understanding VPN limitations helps you make informed decisions about privacy protection rather than relying on marketing claims that promise unrealistic protection levels.
The goal isn’t perfect anonymity (which is practically impossible for most people) but reasonable privacy protection against the most common threats you may actually face.

Frequently Asked Questions
Thanks for reading!
If you found this helpful, like it, share it, and check out more of our content.
About The Author
Nikolas V.
Deviate Solutions LLC
I’ve spent years navigating computer science, digital marketing, business development, and day trading; chasing entrepreneurship and independence. Now I help businesses grow and expand through the latest technology and industry strategies. With all I learn and experience, I use my platform to break down complex insights so you can think differently about technology, your business, and your finances. Everything I share comes from real experience and plenty of trying and failing. Failure is part of the game. Always take the shot, Let’s learn to win together.
Get In Touch